The Security Issue of ICS: The Use of IT Infrastructure
- DOI
- 10.2991/jrnal.k.210521.007How to use a DOI?
- Keywords
- Industrial control systems; programmable logic controller; information technology; network security; Ethernet
- Abstract
With the trend of Industry 4.0, the communication established by Ethernet is becoming more and more common in the Industrial Control System (ICS), and it brings not only pros but also cons like vulnerabilities from information technology. Furthermore, most devices in the ICS are not ready for cyberattacks, and it opens up opportunities for attackers. We generalized a procedure of attacking an Ethernet-enabled ICS and implemented it to the real industrial system we obtained. The procedure gets the information and access of the devices in the ICS, like identifying the manufacturer of Programmable Logic Controllers (PLCs) and overwriting the configuration of PLCs.
- Copyright
- © 2021 The Authors. Published by Atlantis Press B.V.
- Open Access
- This is an open access article distributed under the CC BY-NC 4.0 license (http://creativecommons.org/licenses/by-nc/4.0/).
1. INTRODUCTION
Because of Industry 4.0 [1], Information Technology (IT) is getting more and more widespread in the Operation Technology (OT) field in the modern Industrial Control System (ICS), and serial communication is becoming incompetent to meet the demands. Therefore, in terms of communication of IT in ICS, Ethernet is coming to the most popular one. Ethernet is commonly used in ICS with IT. Comparing to serial connection, Ethernet has much more flexibility and scalability. For example, to access and manage multiple devices, all you need to do is connecting your Engineering Workstation (EWS) to the network where devices are. Also, Ethernet allows hundreds of devices to communicate with each other. In addition, there have been many industrial protocols supporting Ethernet and Internet Protocol.
Although Ethernet meets the demands of IT and OT, it also brings vulnerabilities to ICS. Considering the cost of building information security, most ICS defense mechanisms only have an external firewall, isolation from the office network, or complete independence from other networks. Moreover, for the purpose of operation stability, many running operation systems are not updated to the latest version including the security patches. Therefore, those devices are very vulnerable to malware. Let us take Taiwan Semiconductor Manufacturing Company (TSMC) for example. TSMC is the most advanced integrated circuit manufacturer in the world, and they have the top of cyber security standards to protect the intellectual property and factory operation. However, an accident occurred in 2018. Because of the operational errors during the software installation on the new equipment, after the new equipment hooked up to the internal network, the ransomware infected other computer systems and fab tools and caused about $170 million US dollars losses [2].
In this paper, we show the weakness of information security inside the ICS network by an attacking procedure we generalized and carrying the procedure out on an ICS which was used in the real field before. Eventually, we compromised the Programmable Logic Controllers (PLC) in the ICS network with MODBUS Transmission Control Protocol (TCP) packets. We successfully read and wrote the registers in the PLC and stopped the running PLC.
2. BACKGROUND
Industrial control system is a universal term standing for the control system of the automatic process in the industry, such as supervisory control and data acquisition (SCADA) and distributed control system (DCS). The controller is used to receive and control the information and motion of field equipment such as the value of temperature and motion of the motor. One of the common controllers in ICS is the PLC. Generally, there are digital/analog inputs and outputs on a PLC, and the same model of PLC can be applied to various scenarios with corresponding programs on it.
There are devices controlled in ICS, and there must be some methods for the controller to communicate with each other to make those devices work together. We can divide it into the physical connection part and the communication protocol part. For the physical connection in ICS, there are several standards like RS-232, RS-422, RS-485, and Ethernet. Among those standards, Ethernet is the focus of this discussion due to the trend of IT. For the communication protocols in ICS, there are various protocols based on different standards. Many relatively modern protocol versions are based on Ethernet. Some of them are based on Internet Protocol, such as MODBUS TCP and Ethernet/IP, and some of them are not, such as EtherCAT and PROFINET. For the following discussion, we will focus on MODBUS TCP.
2.1. Industrial Ethernet
In addition to Ethernet interfaces on the ICS devices like PLC and Human Machine Interface (HMI), Ethernet switches and cables are also needed to build the network, and there are some differences between common and industrial Ethernet products. Depending on the different environments, the industrial cables may have high-quality foil and braid to protect data transmission from electromagnetic interference (EMI) [3], use cable jackets with different materials like fluorinated ethylene propylene (FEP) and thermoplastic elastomer (TPE) for durability [4], or have M12 and M8 connectors instead of common 8P8C (commonly called RJ45) to be waterproof. Besides the difference of the connectors, the industrial Ethernet switches have other features comparing to common switches. Let us take Cisco industrial Ethernet 4000 series switches (IE-4000) [5] for example. IE-4000 can work in extreme environments and temperature range (−40 to 70°C), has a durable design, support power over Ethernet up to 240 W, and so on.
To sum up, the main difference between industrial and common Ethernet products is the durability in different environments and the features in use and management. There is no change to the data transmission standards.
2.2. MODBUS Messaging on TCP/IP
MODBUS is a popular communication protocol in industrial environments because it is opened and does not need a license fee. The Protocol Data Unit (PDU) of MODBUS is simple. It only consists of function code and data. Depending on the function codes and request or response, the following data structure is different. For example, function code 03 is reading multiple holding registers, the request data structure is composed of 2 bytes starting address and 2 bytes quantity of registers, and the response data structure is composed of 1 byte following data size and the value of registers [6].
MODBUS Messaging on TCP/IP, or MODBUS TCP for short, as the name suggests, is MODBUS implemented on the Internet Protocol Suite commonly known as TCP/IP (Figure 1), and the port number of it is 502. The data frame of MODBUS TCP is composed of six parts (Figure 2). Transaction identifier is for pairing the request and response. Protocol identifier is used for internal system multiplexing, and value 0 stands for MODBUS protocol. The length field is the byte count of the rest part including unit identifier, function code, and data field. Unit identifier is used for the internal system routing purpose. Function code and data field are MODBUS PDU [7].
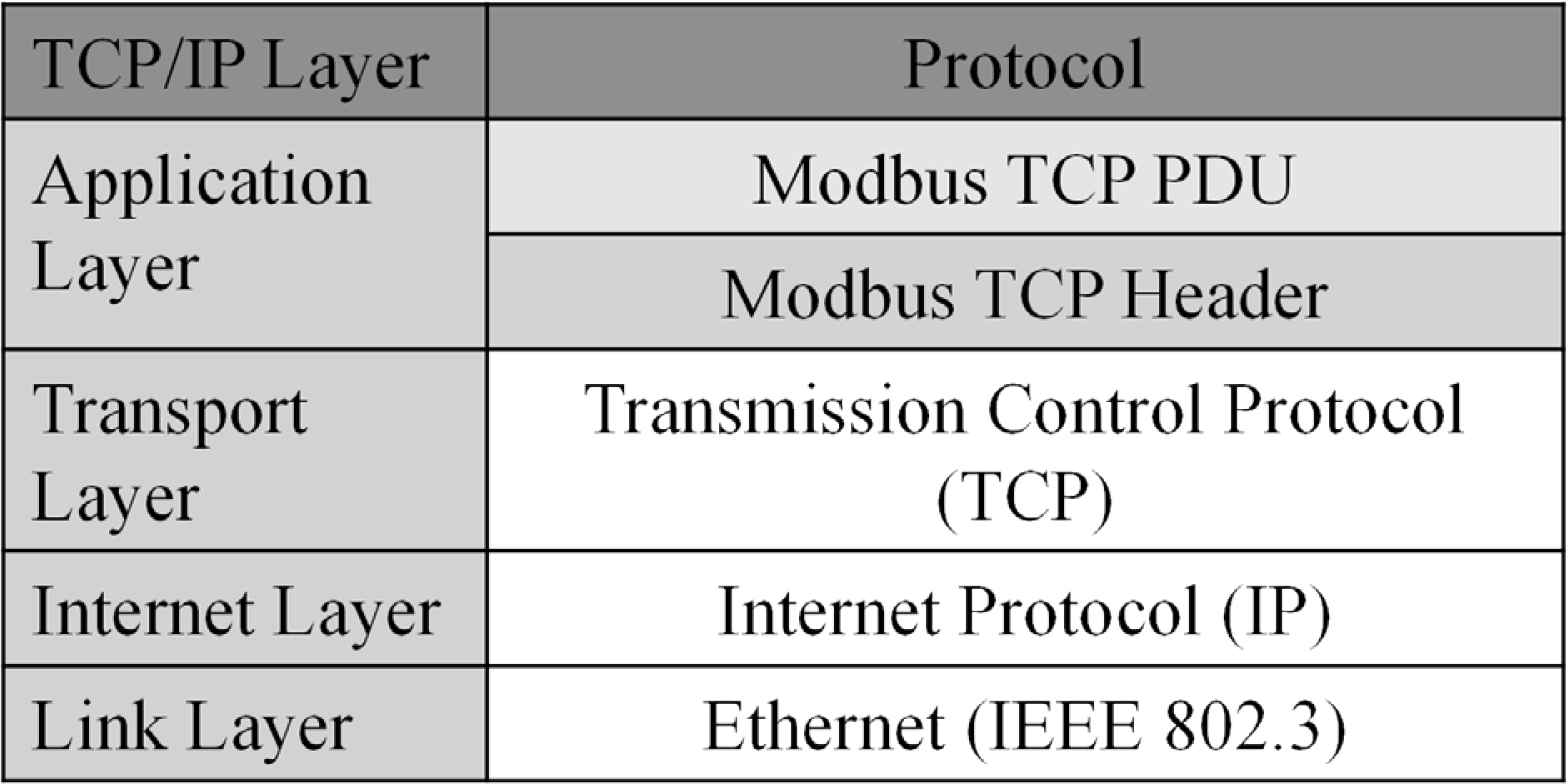
MODBUS on TCP/IP.
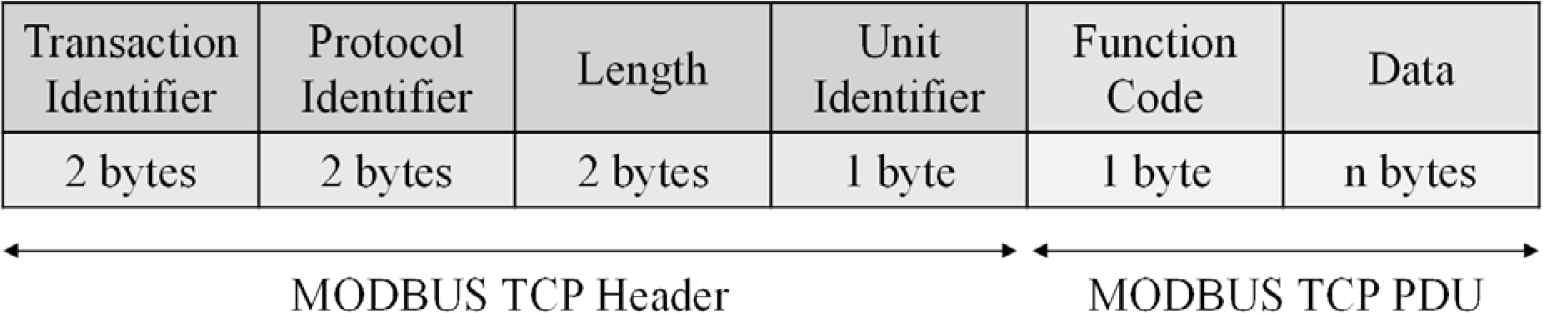
MODBUS TCP data frame.
3. ATTACKING AN ETHERNET-ENABLED ICS NETWORK
3.1. Scenario
Since ICS with IT brings vulnerabilities, the attacker could use those vulnerabilities to inject a backdoor into the computers in the ICS, bypass the information security protection measures, and perform malicious operations. For example, due to the vulnerabilities from IT, an attacker could implant a Trojan horse into the EWS in the ICS via social engineering to bypass the firewall and invade into the ICS network. After the attacker gain the access to the ICS network, the attacker can perform any malicious operations on the ICS. Therefore, assuming that the attacker is able to access the ICS network with some method like backdoor, we generalized a procedure to get the information of the ICS and attack it (Figure 3).
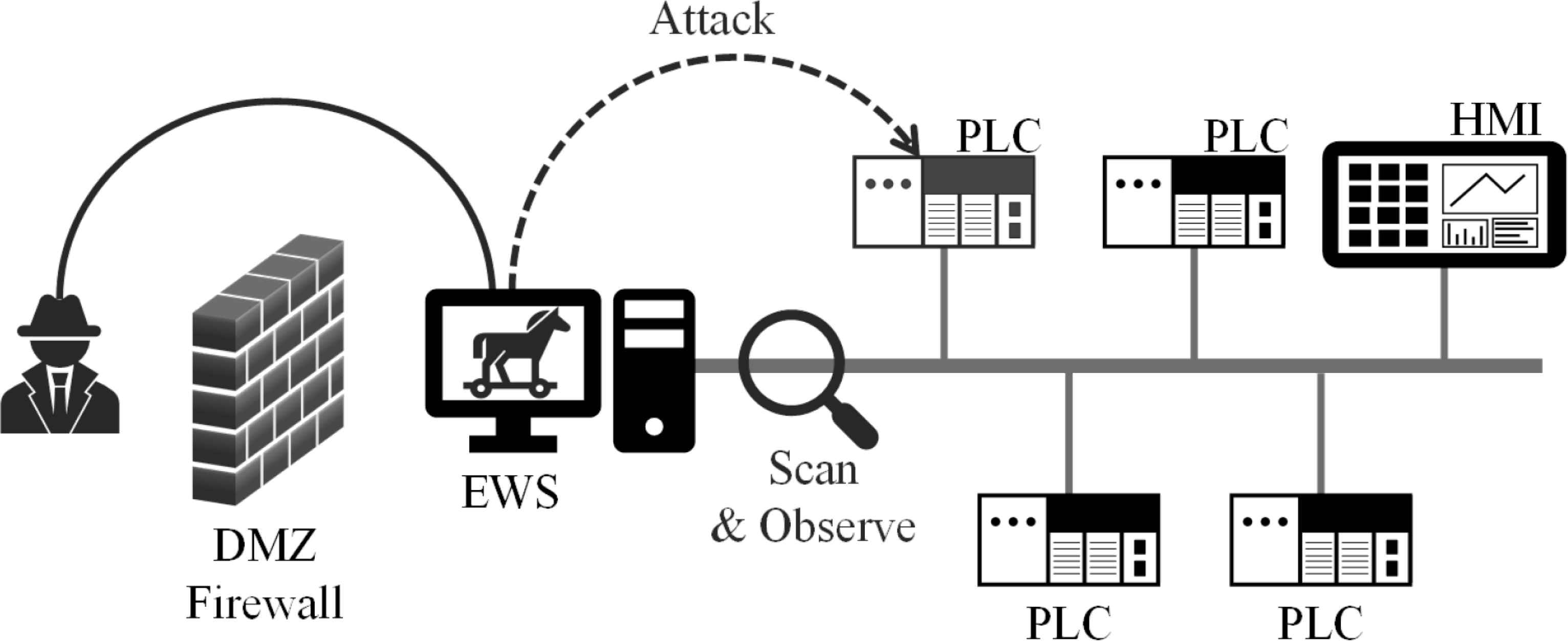
The scenario and procedure of attack in an Ethernet-enabled ICS network.
3.2. Procedure
The first thing to do is scanning the internal network. In most internal ICS networks, due to the weakness of IT security in ICS, there is no protection method like intrusion detection system (IDS) and intrusion prevention system (IPS). Therefore, by scanning the network, the attacker can observe the information in the ICS network such as enabled services, subnets’ range, the number of devices, manufacturer of devices, and so on. After obtaining the information of the ICS network, according to the information, the attacker can formulate detailed attack methods such as man-in-the-middle attack with Address Resolution Protocol (ARP) spoofing to compromise the information security and operation safety in the ICS.
4. CASE STUDY
The ICS that we are going to demonstrate the procedure on is the same as our previous study [8]. The ICS is composed of tens of PLCs to control the field equipment and one computer as the HMI to gather data and control PLCs. All of them are connected to an Ethernet switch.
First, we used a tool called Nmap to scan the ICS network. In the result, we can see the information of online devices, such as IP address, enabled services, and MAC address, and we can identify that the manufacture of PLC is Telemecanique Electrique which is Schneider Electric from the MAC address. Therefore, we speculated that the communication protocol of the PLCs is MODBUS, because MODBUS is widely used in products of Schneider. We tried to read the holding registers with standard MODBUS function code 03 with the MODBUS TCP testing tool, and we succeeded to read the values. With this operation, the confidentiality of the system is compromised. Furthermore, the writing holding registers’ function code 16 also works. We succeeded to change the values of registers. With this operation, the integrity of the system is compromised, and the availability may be affected.
In our previous study, we used the integrated development environment (IDE) called TwidoSuite to perform some malicious operation on the PLC. This time, we use a tool called Wireshark to record the MODBUS TCP packets between the IDE and the PLC, and then try to repeat the attack. Unlike the standard MODBUS TCP, the function code of those packets is 90 (Figure 4), which is manufacturer defined. It is not able to just do the replay attack because of the authentication mechanism in the data field of MODBUS PDU corresponding to the function code. However, we found some rules of it. We successfully established the connection and commanded the online PLC to stop. It cannot be restored to the online state through HMI or restarting the PLC. With this operation, the availability of the system is severely compromised.
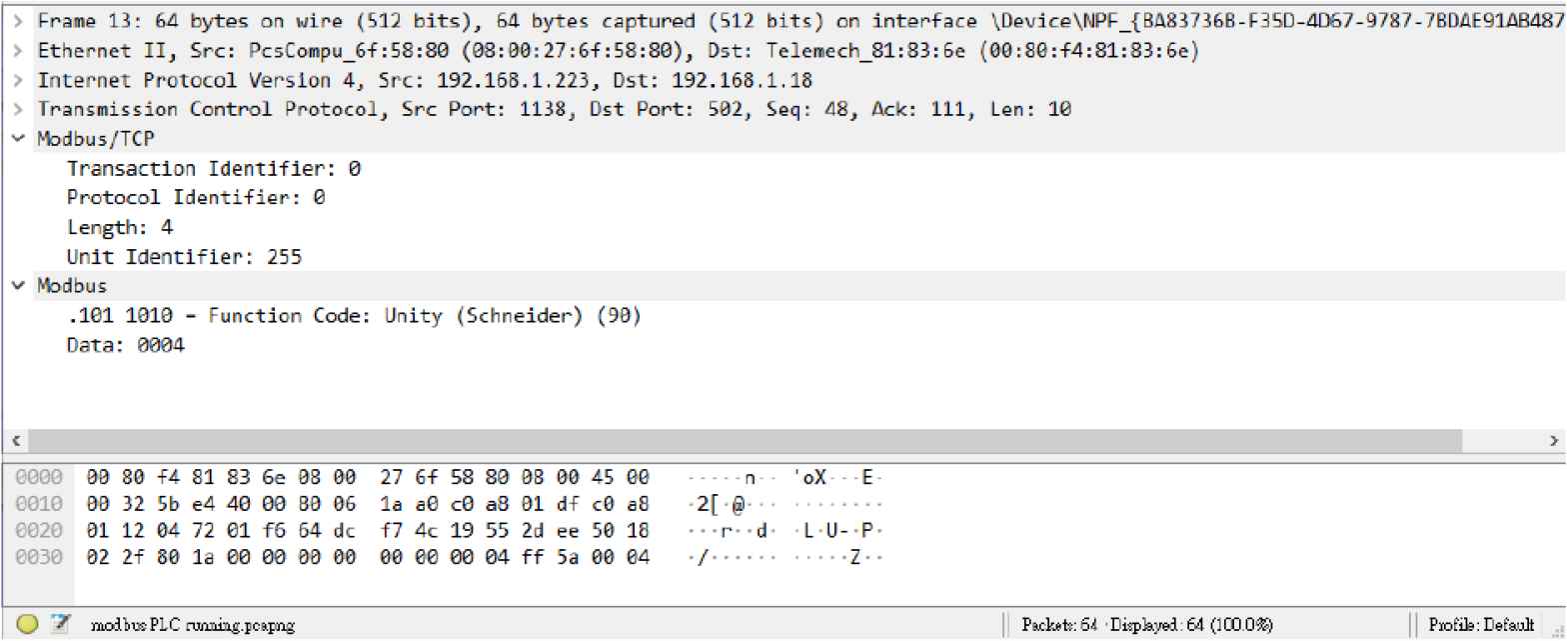
The MODBUS TCP packets with function code 90.
5. CONCLUSION
In this paper, we discussed the weakness of IT security in the ICS network, generalized an attacking procedure for the ICS network, and implemented it to the real industrial system to support the argument. It turns out that we can easily obtain the information of the ICS with the procedure in the certain scenario without the knowledge of the ICS. As the widespread use of IT infrastructure in ICS, we must pay more attention to the cyber security in ICS.
CONFLICTS OF INTEREST
The authors declare they have no conflicts of interest.
ACKNOWLEDGMENTS
This work was supported by the Ministry of Science and Technology (MOST) in Taiwan under contract numbers MOST 109-2218-E-006-014- and MOST 109-2218-E-006-510-.
AUTHORS INTRODUCTION
Dr. I-Hsien Liu
 He is a research fellow in the Taiwan Information Security Center @ National Cheng Kung University (TWISC@NCKU) and department of Electrical Engineering, National Cheng Kung University, Taiwan. He obtained his PhD in 2015 in Computer and Communication Engineering from the National Cheng Kung University. He interests are Cyber-Security, Wireless Network, Group Communication and Reliable Transmission.
He is a research fellow in the Taiwan Information Security Center @ National Cheng Kung University (TWISC@NCKU) and department of Electrical Engineering, National Cheng Kung University, Taiwan. He obtained his PhD in 2015 in Computer and Communication Engineering from the National Cheng Kung University. He interests are Cyber-Security, Wireless Network, Group Communication and Reliable Transmission.
Mr. Kuan-Ming Su
 He was born in Kaohsiung, Taiwan in 1997. He received his B.S. degree from the department of Electrical Engineering, National Chung Cheng University, Taiwan in 2019. He is acquiring the master’s degree in department of Electrical Engineering / Institute of Computer and Communication Engineering, National Cheng Kung University in Taiwan.
He was born in Kaohsiung, Taiwan in 1997. He received his B.S. degree from the department of Electrical Engineering, National Chung Cheng University, Taiwan in 2019. He is acquiring the master’s degree in department of Electrical Engineering / Institute of Computer and Communication Engineering, National Cheng Kung University in Taiwan.
Dr. Jung-Shian Li
 He is a full Professor in the department of Electrical Engineering, National Cheng Kung University, Taiwan. He graduated from the National Taiwan University, Taiwan, with BS in 1990 and MS degrees in 1992 in Electrical Engineering. He obtained his PhD in 1999 in Computer Science from the Technical University of Berlin, Germany. He teaches communication courses and his research interests include wired and wireless network protocol design, network security, and network management. He is currently involved in funded research projects dealing with optical network, VANET, Cloud security and resource allocation, and IP QoS architectures. He is the director of Taiwan Information Security Center @ National Cheng Kung University. He serves on the editorial boards of the International Journal of Communication Systems.
He is a full Professor in the department of Electrical Engineering, National Cheng Kung University, Taiwan. He graduated from the National Taiwan University, Taiwan, with BS in 1990 and MS degrees in 1992 in Electrical Engineering. He obtained his PhD in 1999 in Computer Science from the Technical University of Berlin, Germany. He teaches communication courses and his research interests include wired and wireless network protocol design, network security, and network management. He is currently involved in funded research projects dealing with optical network, VANET, Cloud security and resource allocation, and IP QoS architectures. He is the director of Taiwan Information Security Center @ National Cheng Kung University. He serves on the editorial boards of the International Journal of Communication Systems.
REFERENCES
Cite this article
TY - JOUR AU - I-Hsien Liu AU - Kuan-Ming Su AU - Jung-Shian Li PY - 2021 DA - 2021/05/28 TI - The Security Issue of ICS: The Use of IT Infrastructure JO - Journal of Robotics, Networking and Artificial Life SP - 29 EP - 32 VL - 8 IS - 1 SN - 2352-6386 UR - https://doi.org/10.2991/jrnal.k.210521.007 DO - 10.2991/jrnal.k.210521.007 ID - Liu2021 ER -
